How to Plan for Compliance for your Product?

In today’s highly regulated business landscape, compliance has become a critical aspect of product development and deployment. Adhering to various compliance standards not only helps a company avoid fines and penalties but also ensures trust and confidence among customers and stakeholders. To effectively plan for compliance, organizations must understand the what, why, and how of compliance, relevant frameworks and identify the ones that best align with their needs.
What is compliance?
On a fundamental level, compliance can be considered as following a rulebook. Compliance means essentially adhering to a set of directives put in place by governing bodies or industry standards. Compliance isn’t just a bureaucratic hurdle; it’s the cornerstone of a robust and ethical business framework. It ensures your product operates legally, ethically, and securely, safeguarding your company and its users.
Why achieve compliance?
From the definition, compliance looks like a negative investment, and the C suite might wonder, why bother? While achieving and maintaining compliance can be resource-intensive, requiring dedicated efforts in terms of time, personnel, and financial investments, there are overarching benefits:
- Compliance is your ninja suit against legal troubles. It keeps you off the courtroom battlefield and away from financial penalties.
- Good compliance is directly proportional to brand reputation, like earning the “Most Trusted” badge in your space.
- Compliance adherence also means winning customer trust. It can be a competitive differentiator, as businesses that demonstrate stringent standards often stand out in the market.
- Adopting international compliance standards can also unlock doors and can be a global expansion gateway.
Building a compliance culture
No matter which compliance framework an organization opts for, the fundamental components remain the same and must be integrated into the organization’s culture:
1. Leadership buy-in
Leadership sets the tone for the entire organization. When top executives not only endorse but actively participate in compliance initiatives, it enforces the message throughout the company. Leadership buy-in ensures that compliance is not perceived as a mere checkbox exercise but as a fundamental aspect of the company’s values. It fosters a culture where adherence to standards becomes ingrained in everyday operations.
2. Communication channels
Open and effective communication channels are vital for the success of compliance initiatives. This includes mechanisms for reporting incidents, sharing updates on security measures, and creating an environment where employees feel comfortable expressing security concerns.
Transparent communication also ensures that everyone in the organization knows the importance of compliance. It facilitates the flow of information, allowing for quick responses to emerging threats and fostering a culture of collective responsibility.
3. Training and awareness
Regular training and awareness programs are crucial for educating employees about compliance requirements, security best practices, and the latest threats. This component aims to empower the workforce with the knowledge to contribute actively to the organization’s security posture.
Knowledgeable employees are the first line of defense against potential security and regulatory risks. Training and awareness programs not only enhance individual capabilities but also contribute to building a proactive and vigilant workforce.
4. Continuous improvement
Compliance is not a static state; it’s a journey of continuous improvement. Regular assessments, feedback loops, and adaptability to changing threat landscapes ensure the compliance framework evolves alongside emerging risks.
Continuous improvement is key to staying ahead of evolving threats and maintaining a resilient security posture. It demonstrates a commitment to staying current with industry standards and best practices.
Types of compliance
There are various categories of compliances, and few may fall under more than one category. Here are the common verticals:
1. Regulatory compliance
1.1 Sector-specific compliance
They are established by national and regional governing bodies to ensure safety, security, risk management, and fair practices, but they carry unique sets of laws and regulations to address an industry’s particular challenges and concerns. For instance:
- Financial regulations: Sarbanes-Oxley Act (SOX) for publicly traded companies
- Medical device regulations: FDA regulations for medical devices in the US
- Food safety regulations: Hazard Analysis and Critical Control Points (HACCP) for food safety
1.2 Data protection and privacy compliance
They focus on safeguarding personal and sensitive information, usually dictating how organizations collect, process, store, and share data, emphasizing the protection of individuals’ privacy. For Example:
- General Data Protection Regulation (GDPR) in Europe
- California Consumer Privacy Act (CCPA) in the US
- Health Insurance Portability and Accountability Act (HIPAA) in the US
- Family Educational Rights and Privacy Act (FERPA) in the US
- Digital Personal Data Protection Act (DPDP) in India
2. Customer driven or standard-based compliance
These are voluntary but industry-recognized standards that organizations can implement to demonstrate their commitment to specific principles or practices like product quality, interoperability, and security. Examples include:
2.1 ISO Standards
- Information security management: ISO/IEC 27001
- Business Continuity Management: ISO 22301
- Quality management: ISO 9001
- Environmental management: ISO 14001
2.2 Payment Card Industry Data Security Standard (PCI DSS)
2.3 Service Organization Control (SOC) standards
- Financial reporting: SOC 1
- SOC 2 Type 1 and Type 2 - 5 Pillars : security, availability, processing integrity, confidentiality, and privacy.
3. Environmental and sustainability compliance
They focus on meeting regulations related to environmental protection and sustainable business practices. This includes measures to reduce carbon footprint, waste management, and energy conservation, like:
- Environmental Protection Agency (EPA) regulations
- Carbon Disclosure Project (CDP) reporting
4. Contractual compliance
There are specific requirements outlined in contracts between organizations. They ensure adherence to agreed-upon terms and conditions. For instance:
- Non-Disclosure Agreement (NDA)
- Service Level Agreement (SLA)
5. Internal compliance
This category involves the policies and procedures that are established within an organization to ensure adherence to company-specific ethical guidelines and best practices, like:
- Code of conduct
- Acceptable use policy
- Employee handbook
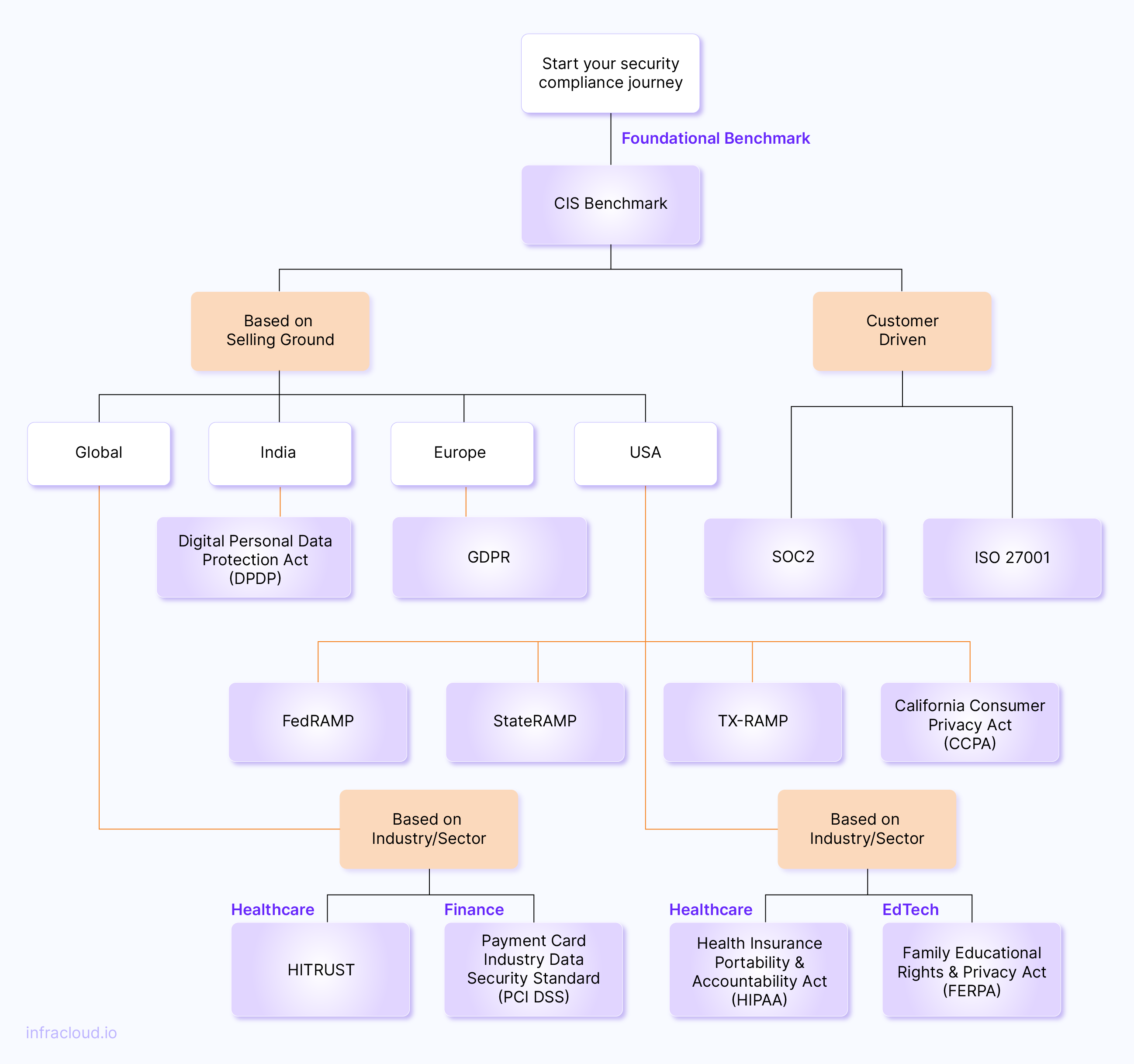
Identifying the right compliance
A misaligned compliance framework can cause issues because while on one side, there is a waste of resources, finances, and efforts, there is also a negative throughput or risk of lapse of the program due to mismatched requirements. Identifying the right compliance framework for a company involves systematically evaluating various factors, considering the industry, nature of operations, and applicable regulations. Some of the common factors are:
1. Understand your industry
For instance, consider the Family Educational Rights and Privacy Act (FERPA) as a specific compliance framework if you deal with educational records. If your company processes credit card transactions, the Payment Card Industry Data Security Standard (PCI DSS) is crucial to ensure compliance.
2. Evaluate business objectives
If innovation and flexibility are key business goals, consider ISO 27001 for information security management, known for its adaptable approach.
3. Selling ground
Depending on your customer base, region-specific compliance may be necessary. For example, A European client may require adherence to the General Data Protection Regulation (GDPR), while a Texas-based client may need TX-RAMP.
4. Consider customer requirements
If you’re a B2B organization with a cloud ecosystem, SOC 2 may help you gain customer confidence. InfraCloud security engineers help clients achieve SOC 2 certification.
5. Assess data handling requirements
If your company deals extensively with health data, consider HIPAA compliance for healthcare information protection.
6. Look at existing frameworks
If the company already adheres to, say, ISO 9001 for quality management, expanding to ISO 27001 for information security management may be a logical step.
7. Consider cost, resource implications, and scalability
For smaller companies with limited resources, adapting to the CIS benchmark or NIST CSF 2.0 framework can be a good starting point to lay down security best practices. When you wish to achieve multiple certifications, focus on the underlying framework it is based on. For example, NIST-SP 800-53 can be adopted by mature teams aiming for ISO, SOC 2, and StateRamp in the pipeline.
Below is a brief flowchart to help you navigate these steps.
Stages of compliance implementation
Once a compliance framework is identified and finalized, the next step is to plan the implementation, which typically involves several stages, from listing the necessary controls to defining roles and responsibilities and creating an improvement and monitoring plan. Each stage is critical for establishing and maintaining a robust compliance program. Regardless of which framework you opt for, below is the key, high-level structure.
1. Listing compliance control requirements
The first step would be scoping the specific control requirements for the chosen framework. Each compliance framework has a set of controls and best practices that must be implemented to achieve compliance. Review the latest revision of the framework and identify the controls that apply to the product.
Objective: Define the specific control requirements and measures required to achieve compliance with the selected framework.
Activities:
- Break down the compliance framework into actionable control requirements.
- Establish control objectives and guidelines.
Suggested platforms: CIS Critical Security Controls® v8, NIST SP 800- 53, NIST CSF 2.0
2. Defining roles and responsibilities
To ensure the successful implementation of compliance controls, it’s essential to define clear roles and responsibilities within your organization. Identify the individuals or teams responsible for implementing and maintaining each control. This ensures accountability and facilitates effective coordination during the compliance implementation process.
Objective: Clarify and allocate roles and responsibilities for compliance management throughout the organization.
Activities:
- Establish a matrix of the Compliance Governance model.
- Define the roles of compliance function teams, security and GRC teams, engineering teams, and non-technical function teams.
3. Gap analysis and identification
After listing the compliance control requirements, conduct a gap analysis to identify any missed controls or areas where your organization currently falls short. This analysis helps you understand the gaps between your existing practices and the required controls. It enables you to prioritize and plan for the implementation of missed controls. Gap analysis can be a manual process by conducting interviews with all relevant teams, or it can be partly automated using compliance management platforms available in the market.
Objective 2: Identify the gaps between current practices and the required controls outlined in the chosen compliance framework.
Activity: Conduct a thorough gap analysis in three verticals:
- Organization-wide: To identify discrepancies between an organization’s existing cybersecurity capabilities and the identified controls in the framework with a specific focus on evaluating adherence to policies, procedures, awareness training, and change management. For example, regarding NIST CSF 2.0, this section is the “Govern” category.
- System/Product gap analysis: It means evaluating the effectiveness of security features in a product or system against the benchmark. This includes controls related to processes, technology, configurations, and the supporting infrastructure.
- IT and Security Operations: Identify shortcomings in IT and security practices like authentication, authorization, logging, and monitoring of networks, endpoints, cloud resources, and personnel, improving incident detection and response.
Suggested tools:
- Manual assessment:
- CIS CSAT CIS Controls Assessment Tool
- NIST Frameworks Cybersecurity and Privacy Reference Tool CPRT
- CIS techstack based benchmarks
- Automation assistance:
- CIS Controls for Secure Kubernetes Clusters: Kube-bench, Checkov, Kubescape, Kubernetes Security Operations Center (KSOC)
- Cloud specific :
- Regulatory compliance in Azure Defender
- Security Health in Google Cloud Security Command Center
- Standards in AWS Security Hub
4. Control implementation plan
Develop a comprehensive implementation plan that outlines the specific tasks, timelines, and milestones for each control. A well-defined plan helps track progress and ensures that compliance activities are executed in a systematic and organized manner.
Objective: Develop a detailed plan outlining the steps and timeline for implementing the identified compliance controls. The plan should include resource allocation and training requirements and address any dependencies for successful implementation.
Activities:
- Create a project plan with clear milestones.
- Allocate resources and define ETA for each control.
- Identify tools and funds required, if any.
- Assign transparent action items for each team member.
- Host training, doubt sessions, and joint calls in case of inter-dependencies
- If your implementation team follows an Agile approach, the plan can be broken down into sprints to track effectiveness.
Suggested tools: Asana, Jira, Azure Boards, Linear, Trello
5. Continuous compliance monitoring: KPI metrics and audit
Regularly monitor the effectiveness of your compliance controls through metrics and audits. Establish key performance indicators (KPIs) to measure the performance and impact of your compliance efforts. Conduct periodic internal audits to assess the effectiveness of controls, identify areas for improvement, and ensure ongoing compliance.
Objective: Implement ongoing monitoring processes to ensure that compliance controls are consistently maintained.
Activities:
-
Establish Key Performance Indicators (KPIs) for compliance.
- Refine processes and SLAs for:
- Patch management
- Change management
- Risk management
- Vulnerability Management
- Conduct periodic internal audits and tabletop exercises:
- User access control audit - suggested quarterly, at least.
- Business continuity management and Disaster Recovery drill - suggested annually, at least.
- Incident response drill - suggested annually, at least.
- Risk register audit - suggested monthly.
- Employee awareness training status - suggested quarterly, at least.
- Onboarding and offboarding activities - suggested quarterly.
- Supply-chain security - suggested annually, at least.
- Monitor changes in regulations and update controls accordingly.
Suggested tools: OpenSCAP, Drata, Vanta, Sprinto, Wiz, Secureframe, Cavirin
6. Achieving compliance certification
Once you are satisfied with the results of internal audits of the controls, you can opt for external audits for the compliance frameworks you’ve implemented. Always double-check that the auditor you choose is accredited by the certification body. Additionally, while you may have reached 100% compliance against controls on your internal scale, there is a fair chance of deviations in what you have implemented versus what the auditor expects, sometimes in the terms of extent to which a control should be adhered, or just the way the control was inferred. Such variations are normal and to be expected in external assessments. You can work with the auditor to patch the remaining gaps and go for a second round of verification. Post the assessment is completed by the corresponding third party, you can expect the certification depending on the timeline shared.
Objective: Engage with the selected external auditor to assess and certify the organization’s compliance.
Activities:
- Select an accredited external auditor.
- Facilitate the audit process to demonstrate adherence to compliance controls.
These stages are cyclical in nature because every compliance framework requires a periodic evaluation. This structure can be used as a baseline and customized variations of the stages can be prepared with automation wherever feasible.
Key considerations for cloud compliance
Irrespective of the framework chosen or the target compliance there are some best practices to adhere to make compliance certificates easier with time.
-
Governance Risk and Compliance (GRC)
- Publish and enforce relevant policies, procedures, and plans to set company-wide guidelines.
- Utilize native cloud security services such as AWS Security Hub, Azure Security Center, or Google Cloud Security Command Center to centralize security management and monitoring.
- Use CNCF tools for policy management, such as OPA, Kubernetes Policy Framework (KPF), Kyverno, etc.
-
Identity and Access Management:
- Centralize authentication, authorization, and accounting (AAA) processes to improve access management and monitor cloud activities. Create dashboards and alert rules wherever feasible.
- Implement RBAC policies to enforce the principle of least privilege and control access to cloud resources based on job roles and responsibilities. Utilize zero trust to ensure access is always denied-by-default.
- Integrate IAM tools with MFA solutions such as Google Authenticator, Microsoft Authenticator, or Duo Security. Enable SSO on internal/third-party platforms and tools used by different teams to the central IAM.
-
Data security:
- Encrypt data at rest and in transit using industry-standard encryption algorithms (e.g., AES-256) to protect against unauthorized access.
- Utilize credential management tools provided by cloud service providers, such as AWS Key Management Service (KMS), Azure Key Vault, or Google Cloud Key Management Service (KMS), to manage encryption keys securely.
- Use metadata tagging to label and categorize data, making it easier to enforce access controls, encryption policies, and data retention policies.
- Implement data redundancy and backup strategies to ensure data availability and resilience against data loss or corruption.
-
Automate, shift left, and collaborate cross-functionally to have a joint, dedicated team for:
- Monitoring and auditing logs
- Vulnerability and patch management
- Incident response
- Penetration testing
-
Role-based training:
- Enforce mandatory training for secure coding practices.
- Provide regular training and awareness programs to educate employees about data security best practices, privacy policies, and regulatory requirements.
Conclusion
Understanding the relevant compliance frameworks, identifying the ones that align with your product needs, and following a systematic implementation approach, you can ensure regulatory adherence and build trust among customers and stakeholders.
However, this is not a one-time solution. Remember to continuously monitor and evaluate your compliance efforts, seek certifications when appropriate, and adapt to evolving regulatory requirements. By prioritizing compliance and embedding it into your product development lifecycle, you can achieve a strong compliance strategy that promotes security, privacy, and trust.
Thank you for reading this blog post, and hope it will help you wear your compliance hat and plan your company compliance program. I would love to hear your thoughts on this post, so start a conversation on LinkedIn. Looking for help with securing your infrastructure or want to outsource DevSecOps to the experts? Learn why so many startups & enterprises consider us as one of the best DevSecOps consulting & services companies.
Stay updated with latest in AI and Cloud Native tech
We hate 😖 spam as much as you do! You're in a safe company.
Only delivering solid AI & cloud native content.