Enhancing Business Security and Compliance with Service Mesh

This blog post was originally published on The New Stack by Ninad Desai, Staff Site Reliability Engineer at InfraCloud.
Microservices have become the go-to approach for building scalable and resilient applications — mainly in the cloud native world. However, the increased complexity of managing communication between these distributed components has given rise to a powerful solution known as service mesh. As a dedicated infrastructure layer, a service mesh provides a comprehensive set of tools and functionalities to streamline and secure interservice communication.
By abstracting away the intricacies of network communication, service mesh offers a centralized control plane that enables fine-grained management, monitoring, and resilience across microservices.
In this blog post, we will delve into service mesh’s pivotal role in managing communication between microservices. By unraveling the capabilities of the service mesh, we can uncover its immense potential for bolstering security measures, enhancing compliance, and facilitating seamless interactions among microservices in modern software architectures.
Security challenges in a microservices architecture
In a microservice architecture, the distributed nature of services introduces unique security challenges.
-
Increased attack surface: Microservices often expose multiple endpoints and APIs, increasing the potential attack surface. Attackers can target specific services, making it essential to secure each service individually.
-
Service-to-service communication: If not encrypted, service-to-service communication can also become a challenge in a microservices architecture, as it is essential to protect the confidentiality, integrity, and authenticity of data exchanged between microservices. Without encryption, network traffic between microservices is transmitted in plaintext, making it susceptible to eavesdropping.
-
Authentication and authorization: Authentication and authorization across multiple microservices can be complex. We have seen many related security breaches like the Marriott Data breach that went unnoticed for 4 years — where an attacker got unauthorized access to their database, exposing the data of up to 500 million guests.
-
Data security: When building cloud native applications, we typically prefer distributing different data received among various services and databases. Securing data at rest and in transit, implementing proper encryption, and ensuring data integrity are essential data-related challenges.
-
Identity and Access Management (IAM): Managing user identities and access control across a diverse set of services can be challenging. So, implementing robust IAM solutions, for example, Okta, etc, is essential.
-
Code vulnerabilities: Smaller codebases in microservices can lead to overlooked security vulnerabilities. Developers sometimes accidentally push sensitive data like usernames-passwords as part of hardcoding.
-
Runtime security: Monitoring and securing services at runtime is vital. One should implement intrusion detection, runtime protection, and anomaly detection to detect and respond to security threats.
-
API security: APIs are the most critical part of microservices. Properly securing APIs, including input validation, access controls, and rate limiting, is essential to prevent attacks like SQL injection and abuse.
-
Service discovery and registry security: Unauthorized access to a service registry could lead to attackers redirecting requests to malicious services. So, securing a service registry and discovery mechanism is important.
-
Logging and monitoring: Centralized logging and monitoring are crucial for detecting suspicious activities and responding to security incidents effectively. However, logging and monitoring for all different types of microservices is an effort.
-
Container security: If you use container-based microservices, you must ensure they are properly configured and isolated to prevent container escapes and privilege escalation attacks.
-
Orchestration security: If you’re using container orchestration tools like Kubernetes to host your microservices then securing the orchestration layer itself is also vital as it hosts your entire apps generally.
-
API Gateway security: API Gateway is a widely used option that needs security to protect incoming and outgoing traffic, including authentication, rate limiting, and payload inspection.
-
Third-party components: Many microservices rely on third-party libraries and components. So securing them is also a big task.
As per Red Hat’s Kubernetes security report, in 2023, almost 90% of survey respondents (engineers and CTOs) experienced at least one security incident in the last 12 months.
In a significant security incident in March 2019, a notable financial institution experienced one of the most extensive data breaches in the history of the United States. The breach resulted in unauthorized access to the personal data of approximately 106 million customers and applicants of the institution. The attacker targeted a vulnerability within the microservices infrastructure of the institution’s application, which was hosted on a cloud platform. As per The Register, the attacker got into Capital One’s AWS storage thanks to a “misconfigured web application firewall.” It is noteworthy that this substantial cyberattack remained undetected for four months before being discovered.
Role of service mesh in improving security
With a service mesh, organizations can establish a strong security posture within their microservices architecture. By leveraging the capabilities of the service mesh mentioned below, they can mitigate risks, enhance data protection, and achieve compliance with industry regulations.
-
Authentication and authorization: Service mesh enables strong authentication and authorization mechanisms. For example, it allows only authorized services to access sensitive microservices and data.
-
Encryption of data in transit: Service mesh protects data in transit using encryption features like mTLS. One can do it with any service mesh tool like Istio, Linkerd, etc. This helps in preventing eavesdropping and man-in-the-middle attacks.
-
Traffic control and routing: Service mesh systems excel in managing traffic flow between microservices. They provide sophisticated load balancing techniques like Round Robin, least connection, IP Hash load balancing, etc., ensuring optimal performance and resource utilization.
-
Access control: Service mesh implements robust access control features, allowing you to define precisely which services can communicate with each other. These access controls act as gatekeepers, regulating the traffic flow and preventing unauthorized services from accessing sensitive microservices.
-
Observability and monitoring: Service mesh emits metrics that can be captured and monitored by various monitoring tools, including Prometheus. Service mesh platforms are designed to provide extensive observability and monitoring capabilities to help you gain insights into the performance and behavior of your microservices architecture.
-
Distributed security policies: It helps with Distributed Security Policies by enabling centralized policy management and enforcement across microservices. It allows you to define security policies, such as access controls and authentication rules, in one place, like a single pane of glass. It also provides a framework for real-time policy updates and changes, reducing the risk of misconfigurations and improving overall security posture.
-
Service identity and authentication: Service mesh also supports JSON Web Tokens (JWT), which can authenticate services and authorize them to access specific resources or perform certain actions within a microservices ecosystem. Services can issue JWT tokens to authenticate themselves to other services or APIs. These tokens can include claims that specify the service’s identity, permissions, and other relevant information.
-
Runtime security and anomaly detection: Service mesh enhances Runtime Security and Anomaly Detection by actively monitoring and protecting microservices at runtime. It continuously observes the behavior of services and network traffic, looking for anomalies or suspicious activities. Service mesh can trigger alerts or automated responses when unusual patterns or security threats are detected.
-
API security: Service mesh also ensures API protection. It can perform input validation on incoming requests to prevent common attacks like injection, ensuring that only well-formed and safe requests are processed by your microservices.
-
Security upgrades and patching: Service mesh uses a sidecar proxies approach, which can be upgraded independently of the microservices they serve. This means you can apply security patches or updates to proxies without recompiling or redeploying the entire application.
Zero trust networking with service mesh
The zero trust security model is a paradigm shift in network security that emphasizes a “never trust, always verify” approach. In traditional network architectures, once inside the network perimeter, entities were often given unrestricted access to resources. However, with the increasing threat landscape and the rise of distributed systems, the zero trust model adopts a more cautious and granular approach.
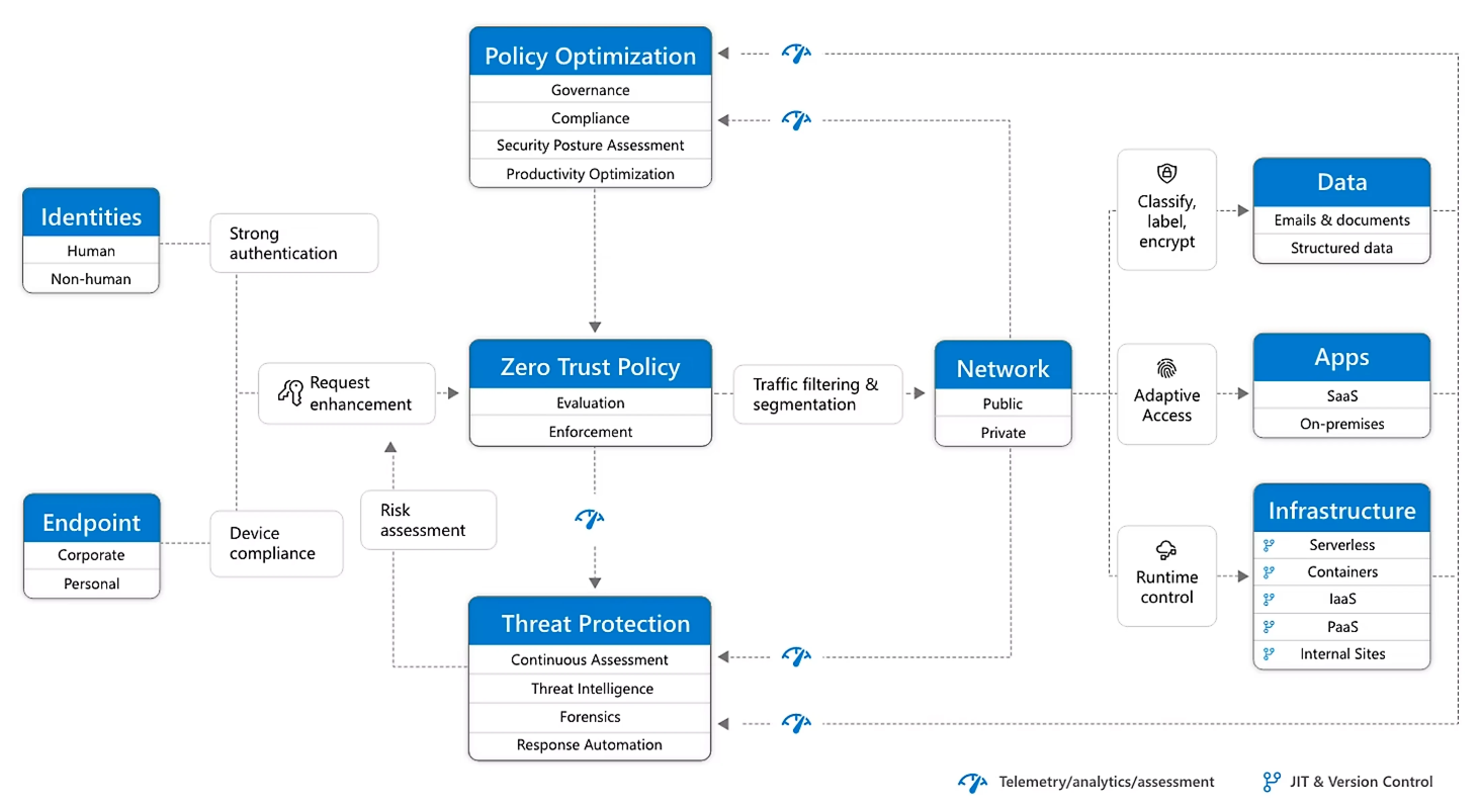
(Modern Security Architecture)
Service mesh plays a critical role in enabling zero trust networking for improved security in microservices architectures. By leveraging the capabilities of the service mesh, organizations can implement zero trust principles at the network level. Service mesh provides a unified control plane that enables fine-grained access control, authentication, and authorization for every interaction between microservices, regardless of location or network boundaries.
With service mesh, all communication between microservices is subject to strict verification and validation, regardless of whether it occurs within the same cluster, across clusters, or even across different cloud providers. Every interaction is evaluated against defined policies and security rules, ensuring that only authenticated and authorized services can communicate with each other. This approach significantly reduces the attack surface and limits lateral movement within the microservices ecosystem, enhancing security and minimizing the potential impact of a
How does service mesh help in aiding compliance?
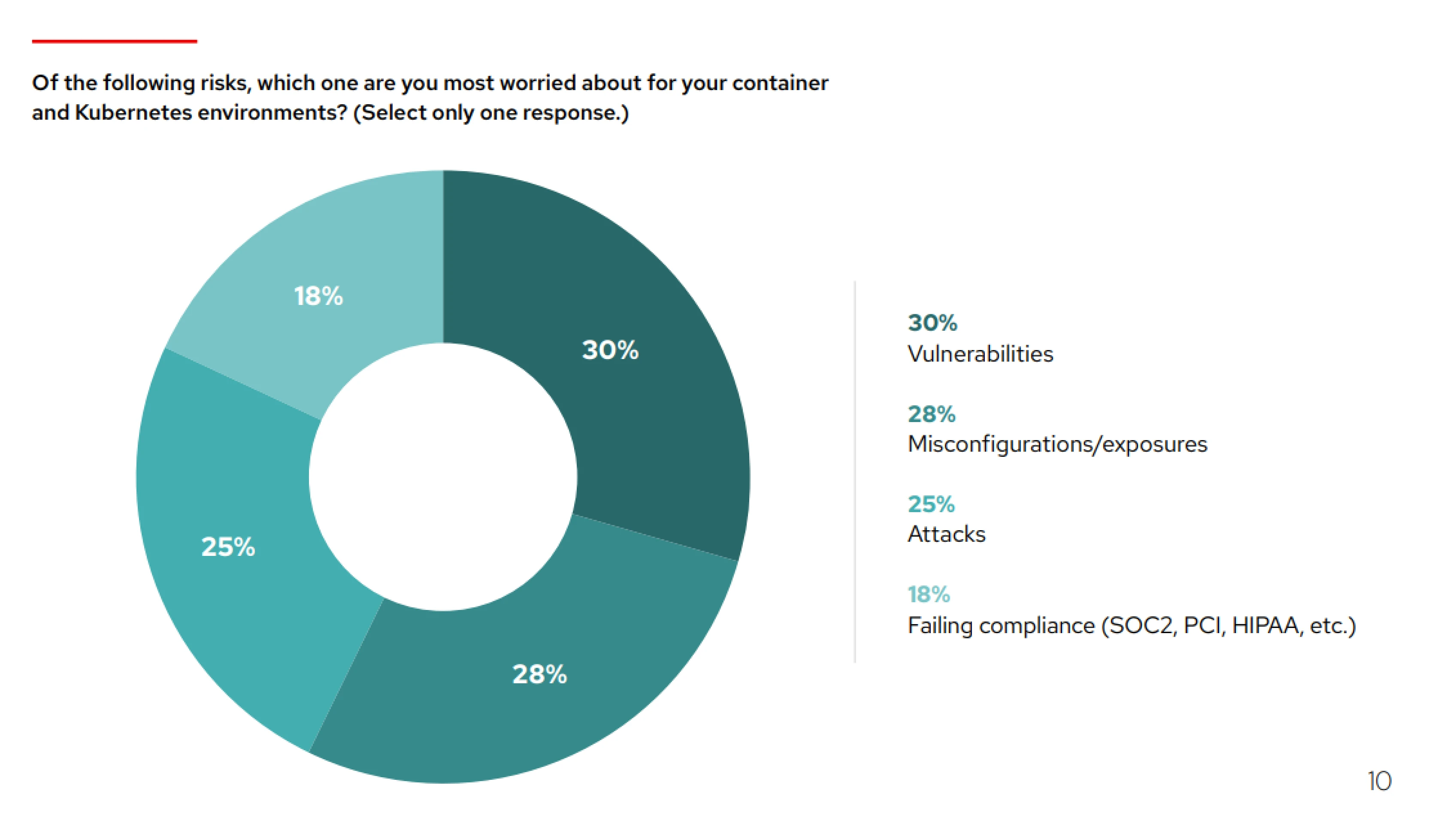
As per the State of Kubernetes security report by Red Hat, almost 18% of organizations are worried about compliance when adopting containers and Kubernetes.
In the landscape of stringent data regulations like GDPR, HIPAA, and PCI-DSS, Service Mesh technologies offer a suite of technical features essential for ensuring compliance while enabling robust application architectures across multiple providers.
-
Policy enforcement: Several service mesh platforms provide robust policy enforcement mechanisms. For instance, Istio’s authorization policy feature ensures compliance with GDPR Article 25 by enabling data protection by design.
-
Access controls: Multiple service mesh solutions offer powerful access control features. Istio, Linkerd, and Consul implement access control mechanisms that allow only authorized entities access to critical information, aligning with compliance standards like HIPAA and PCI-DSS.
-
Auditing and logging: Service Meshes like Istio, Linkerd, and Consul facilitate centralized auditing and logging. These capabilities aid compliance reporting as mandated by GDPR Article 30 and SOX regulations, ensuring comprehensive traceability and accountability.
-
Data encryption (mTLS): Various service mesh providers support mutual TLS encryption. Istio’s Citadel, Linkerd’s mTLS, and Consul’s encryption features ensure secure communication between services, adhering to data confidentiality requirements set by GDPR and HIPAA.
-
Governance and traceability: Tools offered by service mesh providers, such as Istio’s observability features, Linkerd’s telemetry capabilities, and Consul’s monitoring functionalities, aid in monitoring service interactions and ensuring compliance traceability. They provide reliable and consistent in-depth tracing for communication between microservices in the mesh. It also provides configurable real-time dashboards and alerting mechanisms, which can help comply with PCI DSS requirements mentioned in 10.1,10.2.x,10.3.x.
-
Service discovery and segmentation: Service mesh platforms like Consul and Istio provide service discovery and segmentation capabilities that assist in compliance with GDPR’s data residency restrictions. These features ensure data flows align with geographical requirements defined by regulations.
-
Role-Based Access Control (RBAC): RBAC functionalities are supported by several service mesh providers. Istio, Linkerd, and Consul allow defining and enforcing role-based access policies, and enforce role-based access policies to comply with security standards like NIST SP 800-53, GDPR’s requirement around data confidentiality.
Service mesh deployment considerations and best practices
When implementing a service mesh, there are several important factors you should consider for secure and compliant deployment.
-
You should carefully evaluate the security features and capabilities of the chosen service mesh framework. Look for strong authentication methods like mutual TLS and support for role-based access control (RBAC) to ensure secure communication between services.
-
Establish clear policies and configurations for traffic management, such as circuit breaking and request timeouts, to mitigate the risk of cascading failures and improve overall system resilience.
-
Thirdly, consider the observability aspects of the service mesh. Ensure that metrics, logging, and distributed tracing are properly configured to gain insights into service mesh behavior and detect potential security incidents. For example, leverage tools like Prometheus for metrics collection and Grafana for visualization to monitor key security metrics such as error rates and latency.
-
Maintaining regular updates and patches for the service mesh framework is important to address any security vulnerabilities promptly. You should stay informed about the latest security advisories and best practices provided by the service mesh community.
-
Conducting regular security assessments and audits of the service mesh deployment can bring out any compliance gaps. You can align the deployment with relevant regulations such as GDPR or HIPAA by implementing necessary controls, such as encryption for sensitive data in transit and at rest.
By considering these factors and implementing best practices, organizations can deploy a service mesh that ensures secure communication, enhances observability, and meets compliance requirements.
Exploring service mesh in real-world scenarios
We have had the privilege of working with various customers who have embraced the adoption of service mesh in their environments.
For instance, a decision intelligence company that utilizes Kubernetes sought to enforce network policies and gain network-level observability. To address their requirements, we implemented Cilium, leveraging its eBPF-powered capabilities. The inclusion of components like Hubble provided them with a comprehensive network topology graph, enhancing their observability. Additionally, Tetragon, a native runtime security feature within Cilium, bolstered their security measures.
In another instance, we assisted an automotive manufacturer in implementing Istio as their service mesh solution, following the best practices. This deployment enabled them to effectively manage the security of their extensive microservices-oriented infrastructure.
Conclusion
To wrap up, service mesh plays a crucial role in improving security and compliance within modern microservices architectures. By providing robust authentication, authorization, observability, and traffic management capabilities, service mesh frameworks enable organizations to establish secure communication channels, monitor and detect potential security incidents, and meet regulatory compliance requirements.
With the ever-increasing complexity and scale of microservices environments, service mesh becomes essential for organizations to maintain a secure and compliant infrastructure while fostering innovation and agility in their business operations.
I hope you found this post informative and engaging. I’d love to hear your thoughts on this post, so start a conversation on LinkedIn or Twitter.
Stay updated with latest in AI and Cloud Native tech
We hate 😖 spam as much as you do! You're in a safe company.
Only delivering solid AI & cloud native content.